Beware of Spoofed Zoom, Skype, Google Meet Sites Spreading Malware

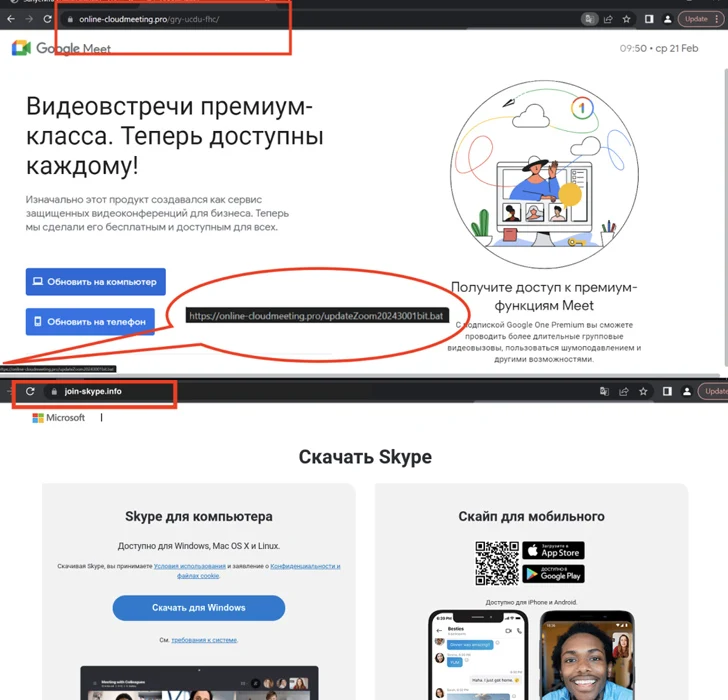
Since December 2023, threat actors have been using fake websites promoting popular video conferencing software such as Google Meet, Skype, and Zoom to spread a variety of malware targeting Android and Windows users.
Zscaler ThreatLabz researchers said: “Threat actors are distributing remote access Trojans (RAT), including SpyNote RAT for Android platforms and NjRAT and DCrat for Windows systems.”
The spoofed websites are in Russian and hosted on domains that are very similar to their legitimate counterparts, suggesting that attackers are using misspelling tricks to lure potential victims into downloading malware.

They also provide the option to download the app for Android, iOS and Windows platforms. Clicking the Android button will download the APK file, while clicking the Windows app button will trigger the download of the batch script.
The malicious batch script is responsible for executing a PowerShell script, which in turn downloads and executes a remote access Trojan.
Currently, there is no evidence that the threat actors are targeting iOS users, as clicking the iOS app’s button takes users to Skype’s legitimate Apple App Store listing.
“Threat actors are using these lures to distribute RATs for Android and Windows that can steal confidential information, log keystrokes, and steal files,” the researchers said.
Meanwhile, the AhnLab Security Intelligence Center (ASEC) revealed that a new type of malware called WogRAT targeting Windows and Linux is abusing a free online notepad platform called aNotepad as a hidden carrier to host and retrieve malicious code.
It is said to be active since at least late 2022, targeting Asian countries such as China, Hong Kong, Japan and Singapore. That said, it’s unclear how the malware spread in the wild.
“When WogRAT first runs, it collects basic information about the infected system and sends it to the C&C server,” ASEC said. “The malware then supports executing commands, sending results, downloading files, uploading those files, etc. Order.”
Meanwhile, a massive phishing campaign orchestrated by financially motivated cybercriminal TA4903 was designed to steal enterprise credentials and potentially launch a Business Email Compromise (BEC) attack. The attacker has been active since at least 2019, with activity intensifying after mid-2023.
“TA4903 frequently conducts campaigns to spoof U.S. government entities in order to steal enterprise credentials,” Proofpoint said. “The actor also spoofs organizations across a variety of industries, including construction, finance, healthcare, food and beverage, and more.”

The attack chain involves the use of QR codes (also known as quishing) for credential phishing and reliance on the EvilProxy Adversary in the Middle (AiTM) phishing kit to bypass two-factor authentication (2FA) protection.
Once a target’s mailbox is compromised, threat actors search for information related to payments, invoices, and banking information, with the ultimate goal of hijacking existing email threads and committing invoice fraud.
Phishing campaigns also serve as conduits for other malware families such as DarkGate, Agent Tesla, and Remcos RAT, the last of which uses steganographic bait to drop malware onto infected hosts.
from Tech Empire Solutions https://techempiresolutions.com/beware-of-spoofed-zoom-skype-google-meet-sites-spreading-malware/
via https://techempiresolutions.com/
from Tech Empire Solutions https://techempiresolutions.blogspot.com/2024/03/beware-of-spoofed-zoom-skype-google.html
via https://techempiresolutions.com/
Comments
Post a Comment