Trezor’s Twitter account hijacked by cryptocurrency scammers via fake Calendly invitation
This is not what you expect to see on the official Twitter account of Trezor, a well-known cryptocurrency wallet manufacturer.
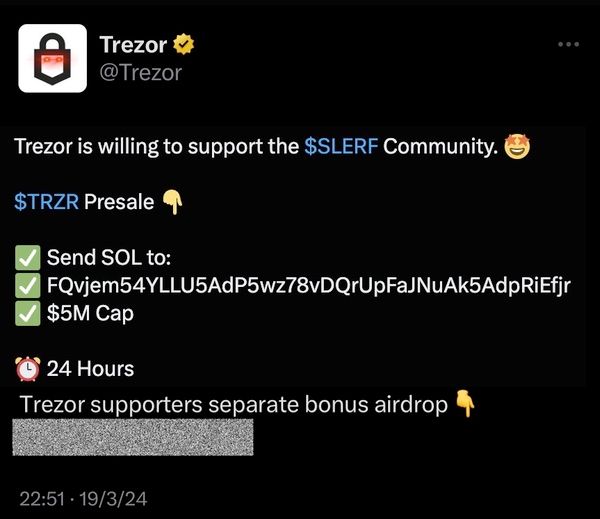
This is a rather blatant attempt to trick unwary cryptocurrency fans into transferring digital currency to a scammer’s wallet.
Whoever hacked Trezor’s Twitter account wasn’t limited to posting hoaxes. They also posted a very offensive message on Twitter.
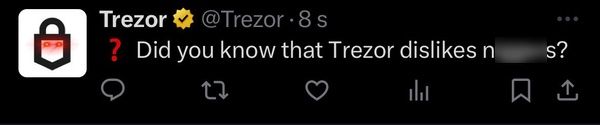
Trezor quickly deleted the unauthorized tweet and posted a warn Its 205,000 followers.
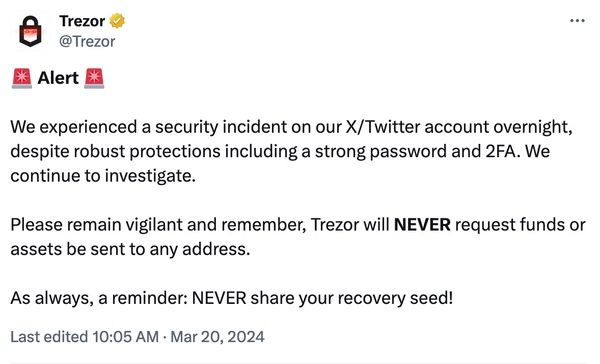
In a subsequent blog post, Trezor explained how its Twitter account was compromised – despite the company taking reasonable security precautions, such as strong passwords and multi-factor authentication.
According to Trezor, someone pretending to be a “trusted entity in the cryptocurrency space” contacted its PR team on February 29, 2024, using a Twitter account with thousands of followers. The imposter requested an interview with Trezor CEO Matej Zak.
After several days of “credible back-and-forth communication,” the attacker shared what appeared to be a Calendly invitation link.
The scam link purported to be a way to schedule a meeting through Calendly, but ultimately led Trezor’s PR staff to Twitter, which asked them to enter their login credentials.
Trezor’s team realized something was wrong and stopped the behavior without compromising their Twitter account.
The attacker then successfully tried again to break into Trezor’s Twitter account.
Pretending a “technical issue” and wanting to reschedule the meeting, someone at Trezor social engineered an authorization request for a fake Calendly app to connect to the official Trezor Twitter account.
Attackers can now use a fake Calendly application to post fraudulent tweets through Trezor’s Twitter account.
Trezor emphasized to customers that only its Twitter account was affected by the security incident:
We would like to emphasize that the safety of all our products is not compromised. This incident in no way affects or compromises the security of the Trezor Hardware Wallet or any of our other products. Your Trezor device and Trezor Suite are still safe to use.
Still, the fact that the company’s Twitter account was exploited by cryptocurrency scammers and posted racist slurs doesn’t bode well.
Be careful when third-party applications ask for access to social media accounts. I have personal experience of my Twitter account being exploited by hackers through rogue third-party services.
Trezor said it revokes all active sessions (kicks out anyone with access to a Twitter account) as well as removes unauthorized posts, and blocks further access by revoking third-party applications.
This isn’t the first time a phishing scam has emerged, tricking companies into clicking on fake Calendly links.
For example, January edge Reports claim that a scammer posed as a journalist and pretended to use Calendly to arrange interviews with targets – all in an effort to drain cryptocurrency wallets.
That same month, a scammer impersonated another journalist and successfully tricked blockchain security agency CertiK into believing they were scheduling meetings through Calendly. The scammers subsequently took control of the company’s Twitter account and posted malicious links.
Sadly, this isn’t Trezor’s first run-in with cybercriminals.
In April 2022, Trezor users received a telling warning that the company had suffered a security breach and that their cryptocurrency wallets could be compromised.
It later emerged that cybercriminals had hijacked control of a newsletter run by Trezor’s MailChimp to issue the warning. The warning attempts to trick users into downloading a malicious, counterfeit version of Trezor Suite.
from Tech Empire Solutions https://techempiresolutions.com/trezors-twitter-account-hijacked-by-cryptocurrency-scammers-via-fake-calendly-invitation/
via https://techempiresolutions.com/
from Tech Empire Solutions https://techempiresolutions.blogspot.com/2024/03/trezors-twitter-account-hijacked-by.html
via https://techempiresolutions.com/
Comments
Post a Comment